|
SecuredMobile Elements
SecuredMobile is a complete management system for operating and securing mobile connectivity across both wired and wireless networks. The technology is comprised of distributed software elements that enable seamless mobility for users across all network types, enforce authenticated access, ensure privacy of communications, and provide efficient administration of network and user devices.
SecuredMobile implementations can range from a simple home office/small office configuration all the way to a complex wide area network with wired and wireless nodes for enterprises and telecommunications carriers.
 |
|
|
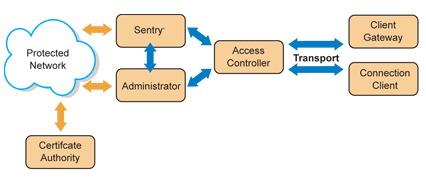
Running in the background of a device, the role of the Connection Client is to manage all aspects of communications between the device and the SecuredMobile infrastructure. The Connection Client initiates authentication of the user to the network, encrypts and decrypts all traffic to and from the device, manages certificate transparency and virtual IP addressing to enable seamless network roaming and connection persistence. In addition, the client can perform compliance checks to enforce your organization's device integrity policies.
|
This optional component is used on networks to eliminate the need for all end-user devices to have Connection Client software installed. The Client Gateway serves as a router to provide a secure connection for an entire network, enabling the benefits of SecuredMobile to be available to any TCP/IP-enabled device, including printers, IP-based security cameras, credit card terminals, RFID badge readers, handheld personal computers, and any non-Windows operating system.
|
The Access Controller functions as a gateway to and from the wireless network, prohibits unauthorized access to the network infrastructure, and routes only authorized traffic to the proper domain. It can also be configured to process new user access requests, and guide them through the process of downloading and installing the Connection Client. When used with wireless networks, the Access Controller operates as a firewall at or near the radio asset to prevent denial-of-service attacks.
|
The Sentry is at the core of managing encryption. Each data packet is automatically encrypted with a private encryption key. The key can be changed at session initiation or as often as every few minutes per the requirements of your security policies. Sentry performs smart IP addressing to locate Clients and transfer packets when Clients use virtual IP addresses on the network.
|
The management core of SecuredMobile, this Web browser-based user interface allows administrators to have remote access to manage all the SecuredMobile software components. You can provision users, including setting encryption key rules and levels, and allocating bandwidth usage quotas. Network partitioning, delegated administration, and reporting mechanisms are also part of Administrator.
|
This element, crucial to the SecuredMobile provisioning process, signs certificates when the Administrator requests a new certificate or a copy of a certificate. The Certificate Authority can either be deployed as part of the SecuredMobile deployment, or hosted by Secured Services.
|
|
 |
 |
|